storware access with cli
Source
https://storware.gitbook.io/backup-and-recovery/administration/cli-reference#overview
https://storware.gitbook.io/backup-and-recovery/administration/cli-v2-reference#vc
Login with cli
Login to vprotect
vprotect login -u <USER>atau
vc login [-p=<password>] -u=<userName>Description
Options
-p, password=<password>* password
-u, user=<userName>* userName
Access-management
Role
Check role privilege and context
List privilege
vprotect rbac -lpor
vc access os prioutput:
APP_BACKUP_SLA_READ, APP_BACKUP_SLA_WRITE, APP_CMD_EXEC_CONFIG_READ, APP_CMD_EXEC_CONFIG_WRITE, APP_INSTANCE_EXPORT_TASK_REGISTER, APP_INSTANCE_READ, APP_INSTANCE_RESTORE_TASK_REGISTER, APP_INSTANCE_RESTORE_TO_NODE_TASK_REGISTER, APP_INSTANCE_WRITE, APP_REPORTING_SEND_EMAIL, APP_REPORTING_VIEW, BACKUPDEST_CLEAN_OLD_BACKUPS, BACKUPDEST_READ, BACKUPDEST_TEST_CONNECTIVITY, BACKUPDEST_WRITE, CLOUD_BACKUP_SLA_READ, CLOUD_BACKUP_SLA_WRITE, CLOUD_DOWNLOAD_READ, CLOUD_DOWNLOAD_WRITE, CLOUD_INSTANCE_EXPORT_TASK_REGISTER, CLOUD_INSTANCE_IMPORT_TASK_REGISTER, CLOUD_INSTANCE_READ, CLOUD_INSTANCE_WRITE, CLOUD_INVENTORY_SYNC_TASK_REGISTER, CLOUD_REPORTING_SEND_EMAIL, CLOUD_REPORTING_VIEW, CLOUD_SERVICE_PROVIDER_READ, CLOUD_SERVICE_PROVIDER_WRITE, CONFIGURATION_WIZARD, DASHBOARD_VIEW, ENDPOINTS_ADMINISTRATION_READ, ENDPOINTS_ADMINISTRATION_WRITE, ENDPOINTS_SERVER_MANAGEMENT_READ, ENDPOINTS_SERVER_MANAGEMENT_WRITE, LOG_READ, MGMT_GLOBAL_SETTINGS_READ, MGMT_GLOBAL_SETTINGS_WRITE, MGMT_PASSWORD_CHANGE, MGMT_RBAC_ACCESS_READ, MGMT_RBAC_ACCESS_WRITE, NODE_CONFIG_READ, NODE_CONFIG_WRITE, NODE_DELETE, NODE_READ, NODE_REGISTER, NODE_WRITE, OS_CREDENTIAL_READ, OS_CREDENTIAL_WRITE, STORAGE_BACKUP_MOUNTED_READ, STORAGE_BACKUP_SLA_READ, STORAGE_BACKUP_SLA_WRITE, STORAGE_INFRASTRUCTURE_READ, STORAGE_INFRASTRUCTURE_TEST_CONNECTIVITY, STORAGE_INFRASTRUCTURE_WRITE, STORAGE_INSTANCE_CLEAN_OLD_SNAPSHOTS, STORAGE_INSTANCE_EXPORT_TASK_REGISTER, STORAGE_INSTANCE_MOUNT_TASK_REGISTER, STORAGE_INSTANCE_READ, STORAGE_INSTANCE_RESTORE_TASK_REGISTER, STORAGE_INSTANCE_RESTORE_TO_NODE_TASK_REGISTER, STORAGE_INSTANCE_SNAPSHOT_TASK_REGISTER, STORAGE_INSTANCE_UNMOUNT_TASK_REGISTER, STORAGE_INSTANCE_WRITE, STORAGE_INVENTORY_SYNC_TASK_REGISTER, STORAGE_REPORTING_SEND_EMAIL, STORAGE_REPORTING_VIEW, STORAGE_SNAPSHOT_SLA_READ, STORAGE_SNAPSHOT_SLA_WRITE, TASK_READ, TASK_WRITE, VE_BACKUP_MOUNTED_READ, VE_BACKUP_SLA_READ, VE_BACKUP_SLA_WRITE, VE_INFRASTRUCTURE_READ, VE_INFRASTRUCTURE_TEST_CONNECTIVITY, VE_INFRASTRUCTURE_WRITE, VE_INSTANCE_CLEAN_OLD_SNAPSHOTS, VE_INSTANCE_EXPORT_TASK_REGISTER, VE_INSTANCE_MOUNT_TASK_REGISTER, VE_INSTANCE_READ, VE_INSTANCE_RESTORE_TASK_REGISTER, VE_INSTANCE_RESTORE_TO_NODE_TASK_REGISTER, VE_INSTANCE_SNAPSHOT_TASK_REGISTER, VE_INSTANCE_UNMOUNT_TASK_REGISTER, VE_INSTANCE_WRITE, VE_INVENTORY_SYNC_TASK_REGISTER, VE_RECOVERYPLAN_SLA_READ, VE_RECOVERYPLAN_SLA_WRITE, VE_REPORTING_SEND_EMAIL, VE_REPORTING_VIEW, VE_SNAPSHOT_SLA_READ, VE_SNAPSHOT_SLA_WRITE
List Context
vprotect rbac -lcor
vc access os conoutput:
ROOT, VIRTUAL_ENVIRONMENT, APPLICATION, STORAGE, PROJECT, CLUSTER, DATA_CENTER, HYPERVISOR, HYPERVISOR_MANAGER, STORAGE_PROVIDER, STORAGE_POOL, APP_CMD_EXEC_CONFIG, CLOUD_SERVICE_PROVIDER, CLOUD_USER, CLOUD_GROUP, CLOUD_SITE, CLOUD_TEAM
Create role
Create the role dengan privilege
vc access role create [-d <description>] -n <newRoleName>
[-sl <isRootAccess>] [-p <privileges>[,
<privileges>…]]…
* -n, –name New role name
* -d, –description New role description
* -sl
, –system-level This action will clear the privilege context tree
* -p, –privilege Role privileges. Split with ‘,’ (with no spaces) or
specified multiple times [-p=PRIVILEGE1
-p=PRIVILEGE2…]
!!!Nb: privileges use “,” without space !!!
Sample:
Name: role-1
Privilege: all access VE instance, all access VE hypervisor, all access Tasks Console
vc access role create -n role-1 -p VE_INSTANCE_RESTORE_TO_NODE_TASK_REGISTER,VE_INFRASTRUCTURE_READ,BACKUPDEST_TEST_CONNECTIVITY,VE_INSTANCE_SNAPSHOT_TASK_REGISTER,VE_INFRASTRUCTURE_WRITE,BACKUPDEST_WRITE,VE_INSTANCE_EXPORT_TASK_REGISTER,BACKUPDEST_CLEAN_OLD_BACKUPS,VE_INFRASTRUCTURE_TEST_CONNECTIVITY,VE_INSTANCE_RESTORE_TASK_REGISTER,TASK_READ,VE_INVENTORY_SYNC_TASK_REGISTER,VE_INSTANCE_MOUNT_TASK_REGISTER,BACKUPDEST_READ,VE_INSTANCE_READ,TASK_WRITE,VE_INSTANCE_CLEAN_OLD_SNAPSHOTS,VE_INSTANCE_WRITE
output:
Property Value
——————- ————————————————————
GUID 92bf1152-3a1a-4997-803b-4533199a546a
Name role-1
Deletable true
System level access true
Privileges [VE_INSTANCE_RESTORE_TO_NODE_TASK_REGISTER, VE_INFRASTRUCTURE_READ, BACKUPDEST_TEST_CONNECTIVITY, VE_INSTANCE_SNAPSHOT_TASK_REGISTER, VE_INFRASTRUCTURE_WRITE, BACKUPDEST_WRITE, VE_INSTANCE_EXPORT_TASK_REGISTER, BACKUPDEST_CLEAN_OLD_BACKUPS, VE_INFRASTRUCTURE_TEST_CONNECTIVITY, VE_INSTANCE_RESTORE_TASK_REGISTER, TASK_READ, VE_INVENTORY_SYNC_TASK_REGISTER, VE_INSTANCE_MOUNT_TASK_REGISTER, BACKUPDEST_READ, VE_INSTANCE_READ, TASK_WRITE, VE_INSTANCE_CLEAN_OLD_SNAPSHOTS, VE_INSTANCE_WRITE]
Contexts 0
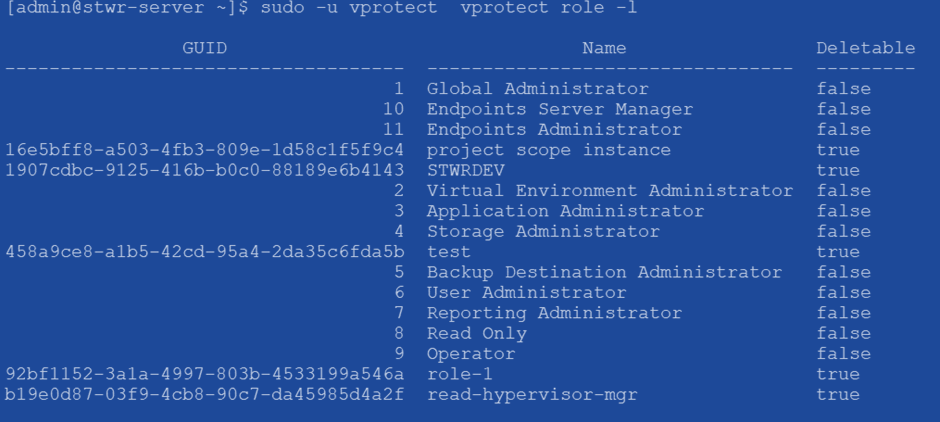
List role exist
sudo -u vprotect vprotect role -lor
vc access role listoutput:
Scope role to context
vc access role context [COMMAND]Commands:
app-config Add application command execution configuration to role
app Add application to role
cloud-group Add cloud group to role
cloud-provider Add cloud service provider to role
cloud-site Add cloud site to role
cloud-team Add cloud team to role
cloud-user Add cloud user to role
datacenter Add datacenter to role
cluster Add hypervisor manager cluster to role
hv Add hypervisor to role
hvm Add hypervisor manager to role
project Add project to role
storage Add storage to role
pool Add storage pool to role
storage-provider Add storage provider to role
vm Add virtual machine to role
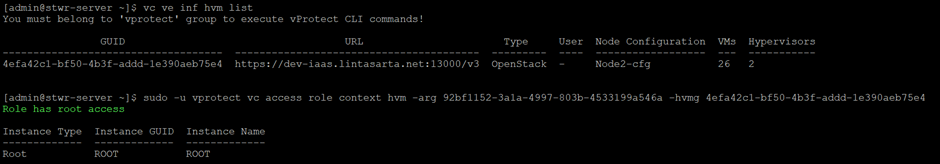
scope role to hypervisor manager
vc access role context hvm (-arg <guid> | -arn <name>…
[-arn <name>…]…) (-hvmg <hvmGuid> |
-hvmn <hvmName>… [-hvmn <hvmName>…]…)
* -arg
, –app-role-guid Application role guid
* -arn
, –app-role-name Application role name
* -hvmg
, –hypervisor-manager-guid Hypervisor manager guid
* -hvmn
, –hypervisor-manager-name Hypervisor manager name
sample:
vc access role context hvm -arg 92bf1152-3a1a-4997-803b-4533199a546a -hvmg 4efa42c1-bf50-4b3f-addd-1e390aeb75e4
output:
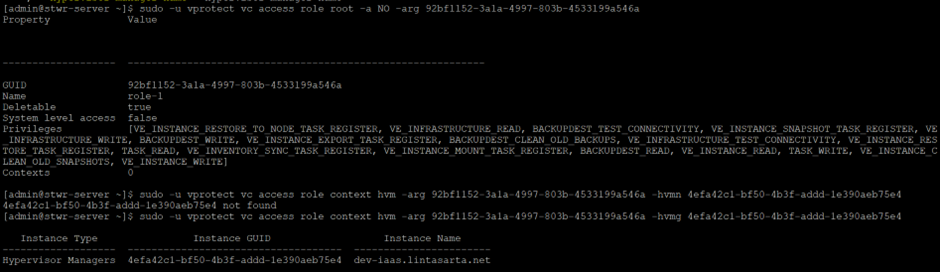
Problem root…
vc access role root -a NO -arg <role_guid>
sample:
Group
Create group
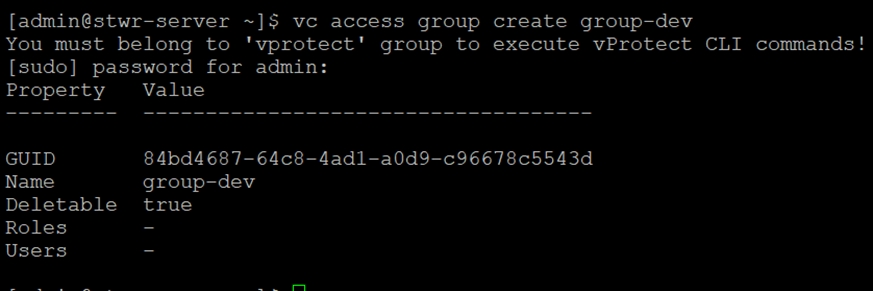
vc access group create <name>
Description
Create group <NAME>
Arguments
<name>
Sample:
USER
Create user
vc access user create [-a <active>] [-g <userGroupGuid>] -l <login>
[-la <language>] -ln <lastName> -n <name>
[-p <password>] -t <timeZone>
* -l, –login
* -p, –password New user password. You can skip this option if you
don’t want to show password in console
* -n, –first-name
* -ln, –last-name
* -t, –time-zone
* -la, –language
* -a, –active YES or NO
* -g, –user-group-guid Access groups for new user
Sample:
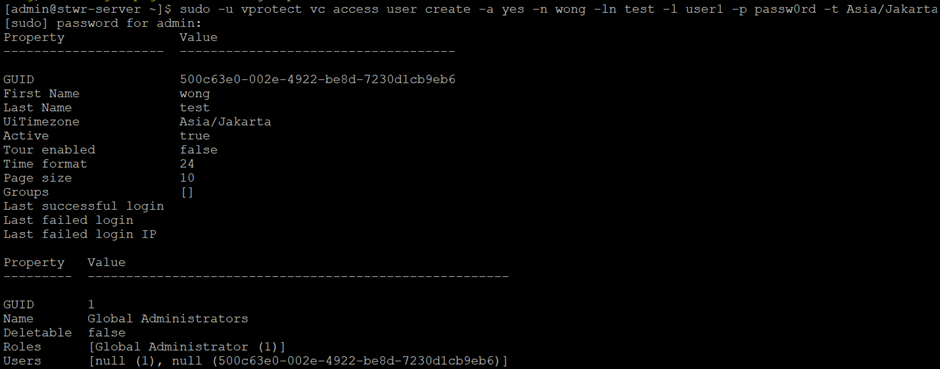
vc access user create -a yes -n wong -ln test -l user1 -p passw0rd -t Asia/Jakarta -g 84bd4687-64c8-4ad1-a0d9-c96678c5543d
output:
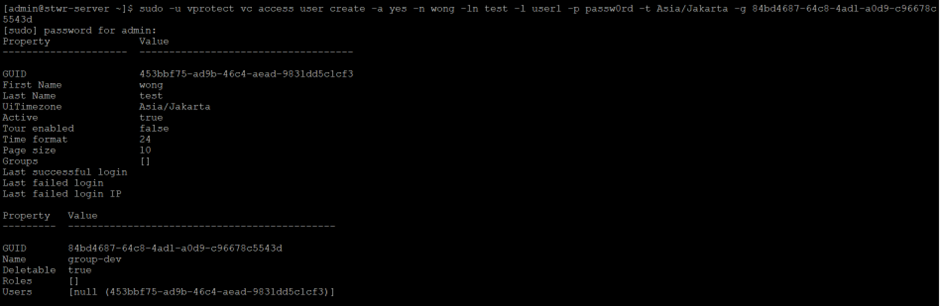
NOTE!!!
Harus pake group, kalo ngga ke set ke Global Administrators